Why Galaxkey
A leading data protection company with military-grade security features for enterprises
Advanced Data
Protection Platform
Galaxkey is a trusted provider of advanced data protection product based on a very strong encryption platform. It secures corporate communications, safeguards data integrity, and supports compliance with global regulations.
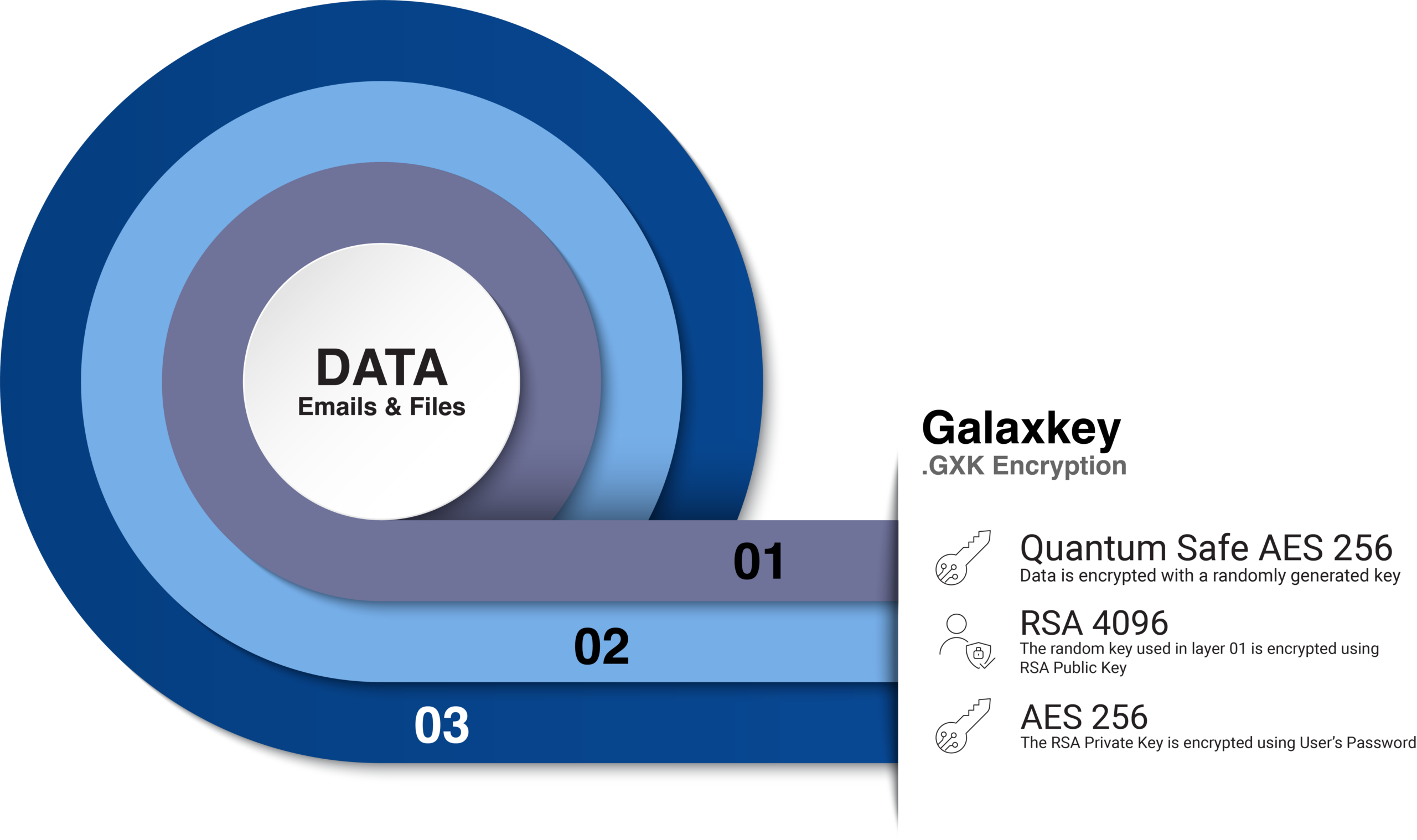
The platform provides complete federated approach when allows businesses to store both the encryption keys and encryption data in total control of the businesses in their own controlled network.
The Galaxkey platform provides a single unified platform to provide solutions for over 95% business to protect data when data is in transit or at rest.
Galaxkey provides a powerful, identity-based encryption platform designed to protect data across all communication channels and storage locations. Whether you’re sending an email, sharing a file, signing an electronic document or securing confidential business documents, Galaxkey ensures your data remains fully encrypted, inaccessible to unauthorised parties, and compliant with global security standards.
Approved by the UK’s National Cyber Security Centre (NCSC), the platform is built on a distinctive identity-based, three-layer encryption framework that grants organisations complete control over their encryption keys. Engineered for seamless integration, the Galaxkey suite is designed to protect both:
With a global network of partners and a team of subject matter experts, Galaxkey is trusted by governments, enterprises, and defence organisations to protect critical information in a rapidly evolving threat landscape.



Key Differentiators
Galaxkey is a Data Protection Platform with unique differentiators. These differentiators sets Galaxkey as an ideal choice for businesses to not only protect their data but also save huge costs.
Data-Centric Security
Encryption persists with the file; even when downloaded, copied, or forwarded.
3-Layer Zero-Trust Encryption Model
Encryption at creation, in transit, and at rest; independent of network, cloud, or device.
Unified Platform
Secure email, file protection, large file transfer, collaboration, and eSign in one consistent platform.
Seamless External Collaboration
Suppliers and partners can access secured content without accounts, plugins, or software.
Independent & Sovereign Vendor
Not tied to hyperscalers; outside CLOUD Act scope; no external data-sharing obligations.
On-Premise Setup
Aligns with global sovereignty and regulatory requirements.
Customer-Owned Key Management
Business maintains exclusive control of encryption keys; even Galaxkey cannot access data.
Federated Approach
Galaxkey’s federated security model ensures that businesses can manage their encryption infrastructure without depending on external cloud providers. This enterprise-first approach ensures absolute data sovereignty, enabling businesses to meet compliance, security, and operational requirements seamlessly.
Keep encryption keys inside your infrastructure, ensuring total control over security policies.
Even with federated access to external users, no data leaves your enterprise network.
Businesses can combine on-premises and cloud environments without compromising security.
No Dependence on Networks, Devices, or Applications
Unlike security solutions tied to specific ecosystems like Microsoft Fabric, Galaxkey operates independently, making it highly adaptable for businesses across industries.
Galaxkey’s cross-platform compatibility ensures that businesses can implement data security without disrupting workflows or requiring additional infrastructure changes.
Securely encrypts data whether you’re on corporate Wi-Fi, public networks, or offline systems.
Functions across Windows, macOS, iOS, and Android without limitations.
Encrypts emails, files, documents, and unstructured data across all business tools.
Who Holds & Manages the Encryption Keys?
Galaxkey supports three deployment models, allowing businesses to choose how encryption keys are managed.
This approach ensures maximum data security, whether on-premises or in the cloud.
- Businesses generate and store their encryption keys internally.
- No involvement from Galaxkey—ensuring zero external access.
- Encrypted data remains fully secure, even if stored externally.
- Encryption keys are stored in ISO 27001-certified cloud infrastructure.
- Keys are encrypted with user passwords – ensuring Galaxkey has no access.
- Only authorised enterprise users can decrypt secured files.
This approach ensures maximum data security, whether on-premises or in the cloud.
Key Security Features of Galaxkey
- Hierarchical User Access Management (Administrator, Service Accounts, Standard Users).
- Active Directory & Single Sign-On (SSO) Integration.
- Mass User Provisioning & De-Provisioning for corporate environments.
- Custom Branding & Email Templates for business use.
- NCSC-Certified Email Encryption – UK government-certified security standards.
- FIPS 140-2 Compliant – AES 256-bit & RSA 2048 encryption for data protection.
- Hybrid & On-Prem Solutions allow businesses to generate their own encryption keys.
- Integration with Hardware Security Modules (HSMs), including Thales HSM.
- Group-based encryption policies for corporate users.
- Granular audit logging & GDPR-compliant reporting.
- Custom Data Protection Rules for email encryption and file security.
- Regular Expression Support for Data Classification.
- Integration with Active Directory, Azure AD & Okta for seamless user management.
- Biometric Identity Verification with Yoti.
Why does your business need Galaxkey?
Data protection and security is non-negotiable. Businesses must protect sensitive information from cyber threats, ensure compliance with stringent data regulations, and retain control over their encryption keys. Galaxkey provides an all-in-one solution for securing emails, files, and digital transactions while remaining independent of third-party platforms and offering cost-effective security at scale.
Instead of purchasing multiple security solutions for different aspects of data protection, Galaxkey offers a single platform that covers:
Email Encryption – Securely send and receive encrypted emails.
File Encryption & Secure Storage – Protect sensitive files on local devices or cloud storage.
Secure Digital Signatures – Legally sign and verify documents without extra licensing fees.
Secure File Sharing & Collaboration – Share protected files while maintaining encryption.
Federated Data Discovery & Compliance Monitoring – Monitor sensitive data in-house with AI-driven security policies.
With Galaxkey, businesses can consolidate their security efforts under one cost-effective solution, eliminating the need for multiple vendors.
Unlike many encryption solutions that are tied to Microsoft Fabric, Google, or other third-party cloud services, Galaxkey operates independently, allowing businesses to:
Encrypt any form of unstructured data – Emails, files, documents, and database records.
Deploy in any IT environment – Whether on-premises, private cloud, or hybrid setups.
Use any device, anywhere – Works across Windows, macOS, iOS, and Android without restrictions.
Avoid vendor lock-in – You are not forced to rely on third-party ecosystems to implement security policies.
This ensures greater flexibility, security, and control over your organisation’s data.
Businesses face increasing regulatory pressure to protect customer data, intellectual property, and confidential business information. Galaxkey simplifies compliance with international data protection laws, including:
GDPR (General Data Protection Regulation – Europe) – Ensures that personal data is encrypted and access is restricted only to authorised users.
HIPAA (Health Insurance Portability and Accountability Act – USA) – Protects patient health information (PHI), meeting strict healthcare security standards.
CCPA (California Consumer Privacy Act – USA) – Helps organisations comply with data privacy laws by securing consumer data.
PDPL (Personal Data Protection Law – Middle East & Other Regions) – Enables businesses to meet data sovereignty requirements while maintaining secure encryption standards.
ISO 27001 Compliance – Meets global best practices for information security management.
With built-in compliance reporting and automated audit logs, Galaxkey ensures businesses avoid legal risks and regulatory fines.
- Businesses retain control over encryption keys, even if data is stored in external environments.
- Galaxkey has zero visibility into user encryption keys, ensuring maximum data security.
- Federated security model allows for on-prem, hybrid, or private cloud deployments.
Unlike traditional cloud-based encryption providers, Galaxkey gives businesses the flexibility to host encryption infrastructure in-house, ensuring complete data sovereignty and regulatory compliance.
Easy Deployment – No complex configurations or dependencies on third-party software.
Minimal Training Required – Simple user interface that integrates into existing workflows.
Works Across All Business Sizes –From small businesses to large enterprises, Galaxkey provides scalable security solutions.
